

To provide safe and reliable medical services, it is important to have high economic efficiency in addition to high quality of care. However, the quality and economy of medical services are in a trade-off relationship, so we research to quantitatively capture treatment outcomes and apply them to hospital management.

It is difficult to predict the progression of chronic diseases, including when and what symptoms will occur. If prediction becomes possible, patients and doctors can respond proactively to the disease progression. To this end, we aim to predict disease progression using information processing, such as that derived from medical information.

3D Security Planning is software that enables us to provide a holistic security plan for major events by combining 3D visualisation technology, GIS (Geographic Information System) and BIM (Building Information Modelling).
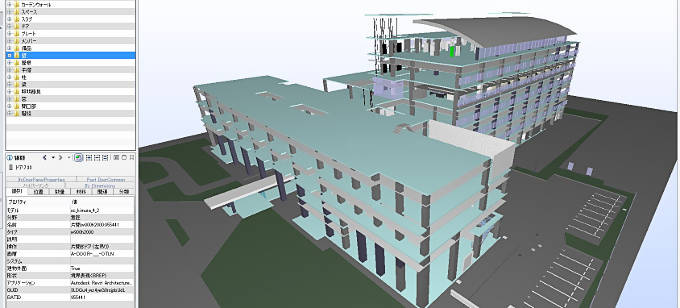
For making mass advanced judgments efficiently, taking advantage of 3D building model data in BIM (Building Information Modeling) is important. But efficient operation of 3D building model data have some problem. To solve this problem, we explore IFC (Industry Foundation Classes) Model Server, which is the platform to manage 3D building model data.

Why do people behave so irrationally, especially in risky or dangerous situations? We believe that evolution is the key to answer this question. By adopting the concept of life history from biology, we are conducting multi-agent simulation to evolve artificial lives and developing a model of human risk behaviors.

To provide safety monitoring services, a detailed understanding of the situation is necessary. To accomplish this, various sensing technologies that use characteristics such as optical and infrared (O/IR) waves, radio waves, and sound waves are required. Through the combination of these technologies, our monitoring technology can recognize various situations involving occupants and goods, both indoors and outdoors.

People can recognize each other by looking at each other's faces. In addition to recognizing a person, faces include attribute information such as age, gender and even emotions. we are developing technologies for secure and convenient services using facial attributes.

As IoT becomes more widespread, more and more devices will be connected and exposed to physically compromised environments. To provide secure and reliable IoT services, IoT devices need hardware security and encryption technologies.
Due to the increase in high performance IoT devices and the increase in amount of communication data, it will be important to solve communication problems in IoT services in the future. By combining services and communication technologies, we aim to realize next generation network technology that can convert and transmit data of IoT devices according to service scenes.

Traditional device management cannot easily scale to the massive number of IoT devices and deliver consistent quality, increasing security risk. We are therefore exploring device management technology that delivers efficiency without manual processes and trustworthiness of the entire system.

Protecting privacy is one of the major challenges in recent years. We are focusing on building an authentication scheme to prove the authenticity of user attributes and enhance privacy preservation. Zero-knowledge Proofs is one of the promising technologies.