
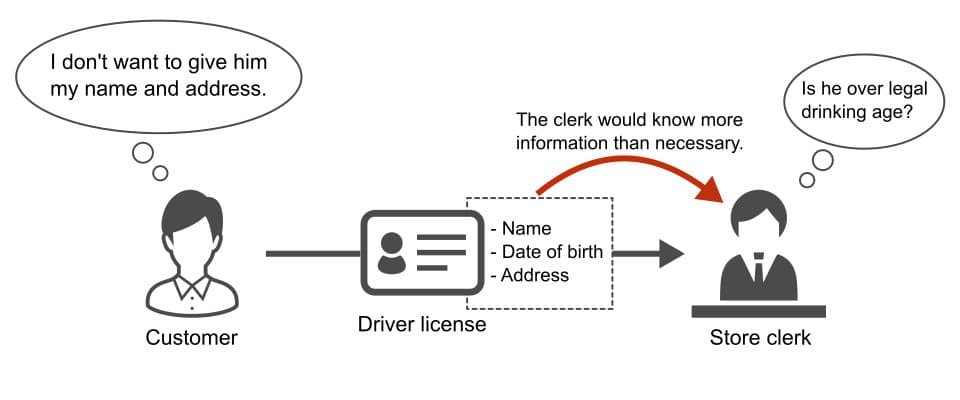
When you buy goods or receive services in real life, a store or a service provider sometimes asks you to present your ID card or some proof documents in order to check your attribute. For example, a store offering alcoholic beverages needs to verify a date of birth described on a document issued by a trusted third party and confirm that you are of legal drinking age.
Similar to cases in real life, there are also cases in digital society that require proof of someone’s attributes. A set of statements about attributes is called a credential, and authenticating a client using a credential, including a digitally-formed one, is called attribute-based authentication.
In a conventional authentication scheme using ID cards, there are two well-known challenges to solve, as follows:
1. Strict Verification of Credentials
In the above example, a clerk in the store checks the ID card presented by the customer, and judges whether the customer can buy alcoholic beverages or not. However, it requires a high level of skill to verify the authenticity of the ID card in detail. It also takes a lot of time and money to perform the verification.
2. Privacy-Preserving Verification of Credentials
As mentioned above, the clerk only needs to know the fact that the age of the customer is over the legal drinking age but does not need to know their date of birth. Besides the date of birth, a lot of personal information, such as an address, may be on the ID card. There is a risk of unintentionally disclosing unnecessary information to the clerk. In general, verification of credentials may potentially compromise a client's privacy if a verifier can obtain more information than necessary in the process.
In the case of cyberspace, e.g., the case of online shopping, the challenges of verifying credentials are more complicated because digital data can be easily forged, and it is easier to impersonate a user than in the real world. However, in recent years, new technologies have been developed to address the challenges of cyberspace.
Using tamper-proof devices such as smart cards is one of the options that can solve the first challenge, Strict Verification of Credentials, to some extent. When a verifier needs a client's credentials for the verification process, the verification software can obtain the client's tamper-proof credentials that are stored in a secure area of the client's device.
Another option is to use cryptographically signed credentials, which is a standard way to ensure verifiability of credentials. The new concept “Verifiable Credentials (VCs)” is attracting attention as a next-generation technology of credentials that has the potential to expand its use in the future.
VCs are digitally-formed credentials in cyberspace that have a similar concept to ID cards and certificates used in the real world. They have tamper-proof features, the same as smart cards and conventional digital certificates, which are verifiable by electronic devices. Moreover, they can apply selective disclosure methods, which enable a credential holder to disclose only necessary information to a verifier. For example, a holder can show only their date of birth and conceal any other information in their credentials. Selective disclosure methods are fundamental to enhancing a client's privacy.
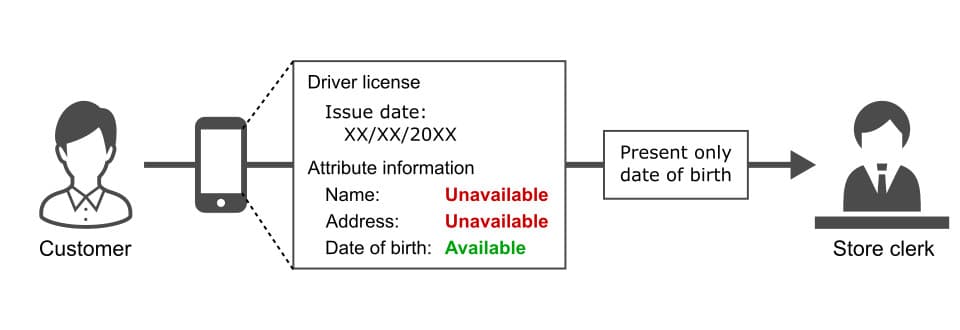
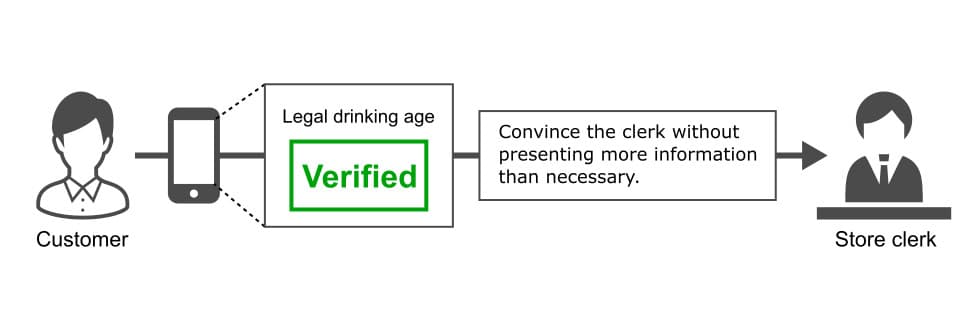
Even if using selective disclosure, a credential holder must present a date of birth for a verifier to confirm that it meets the age limit. Under traditional system environments, a verifier needs to know a client's personal information in order to verify its authenticity, confirm that it meets some condition, and decide to provide goods or services. They cannot perform these procedures if the information is concealed. Thus, it was thought to be difficult to achieve both credential verification and privacy preservation at the same time. However, in recent years, the technology called “Zero Knowledge Proofs (ZKPs)” has built expectations that it will pave the way to solving the challenge. ZKPs are cryptographic primitives, which make it possible to prove the authenticity of a statement without revealing any information beyond the validity of the statement. For example, assuming that a client is 35 years old, lives in Tokyo, and knows their own secret password “Zh8oN17k”, by using ZKPs they can convince a verifier that statements such as “the client is over 20 years old”, “they live in the eastern area of Japan” and “they know the right secret” are true without revealing the above facts.
The basic theory of ZKPs was initially invented in the 1980s, and advanced theories and techniques have been developed since then. The development of theories and improvements in computational power have led to the practical application of this technology in a variety of applications. By combining it with VCs, it is possible to build an attribute-based authentication scheme that ensures privacy preservation.
These technologies are expected to be very useful to society and bring about new innovations, but there are still challenges to overcome for implementation and widespread use. We also need to consider various aspects, including legal regulations, requirements from society and the market, standardization, the restriction of hardware performance, and so on, in addition to the technological theories. The mission of our laboratory is to research technologies and apply them to our services in order to better contribute to society. Our team conducts research from a broad perspective, including not only theories and implementations of technologies, but also related social systems that are essential to building a trust infrastructure for digital society.