|
|
|
|
To interconnect organizations which have different security policies, there must be some form of PKI interoperability. Connecting organizations with differing PKI policies and inter operating with multiple domain PKI are the global issues.
To achieve multi-domain PKI interoperability, the difference between the policies of each domain should be clarified and a typical trust model to establish multi-domain PKI should be shown. I am therefore submitting a proposal as a Internet-Draft with Nelson Hastings (NIST) and Rebecca Nielson (Booz Allen Hamilton) to the IETF (Internet Engineering Task Force) in accordance with our thoughts that these issues are to solved only through a technological solutions but rather as a Best Current Practice.
|
|
| Why do we need to standardize PKI interoperability? |
|
I have worked on several domestic and international PKI interoperability projects. Most of them were a continuing process of trial and error. The question is, what kind of operation, arrangement or agreement is necessary to achieve PKI interoperability between organizations which have different policies?
This may be termed the "now-how"; of PKI interoperability, especially a multi-domain PKI consisting of organizations with differing policies. Although various technical discussions and standards are progressing mainly in the IETF/PKIX WG, interoperability issues, especially concerning multi-domain PKI, are not progressing globally. Since interoperability in multi-domain PKI should be achieved for systems using PKI globally, interoperability issues should also be discussed globally. Therefore, with my experience and the experiences of Nelson Hastings and Rebecca Nielson, we are proposing an internet draft to the IETF for smooth interconnection of global multi-domain PKI.
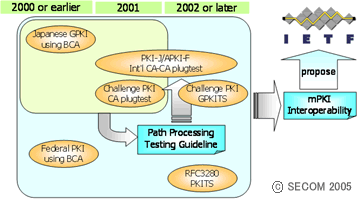
Figure1: Standardize PKI nteroperability
Figure shows the relation between our PKI interoperability projects and the Internet Draft submitted to the IETF for multi-domain PKI interoperability.
In AsiaPKI Interoperability Project 2002, I developed the "(Certification) Path Processing Testing Guideline" based on the experiences of the Japanese government PKI collaborative experiment (2000), multi-vendor CA plug test in the JNSA Challenge PKI Project (2001) and the Cross-border PKI Interoperability Project (2001) in the Asia PKI Forum. On the other hand, NIST has worked on interoperability for the US government PKI and started the operation of the FPKI in 2000. Their efforts are shown in RFC3280 (2002). In Japan the same year (2002), JNSA developed the GPKITS (Government PKI Test Suite) to test conformance to GPKI and in the US, NIST developed the PKITS (PKI Test Suite) to test for conformance to RFC3280. In this regard, both Japan and the US had gathered knowledge and experience for interoperability from CA to PKI application, thus we are submitting our knowledge to the IEFT as a solution for multi-domain PKI interoperability.
|
| What is a multi-domain PKI? |
|
PKI is an infrastructure to establish the trustworthiness in the network world, operating with set policies. A PKI domain is a unit of PKI operating under a certain policy, for example, a local organization PKI policy. The IT security department of the organization will typically design the organization-wide policy, and then each division PKI will be designed in accordance with the company-wide policy. Since the policies of each division are consistent with the company-wide policy, the IT security division can control and manage all division PKIs accurately.
However, this model is centralized and can only work in a local setting. On a global scale, PKI domains are decentralized and there will exist PKI domains with differing policies. Consequently, multi-domain PKI refers to inter operating with these decentralized PKI domains. Even though most policies are nearly identical, the differences must be investigated to access the mutual policy accurately.
The Japanese GPKI is a typical example of a multi-domain PKI. GPKI consists of agency CAs which each have different policies, commercial CAs which similarly have different policies, and bridge CAs which cross-certifies to each other. In addition, the GPKI bridge CA cross-certifies with other PKIs, such as the LGPKI (Local Government PKI) and JPKI (public individual certification service). This the GPKI forms a complicated, large scale multi-domain PKI.
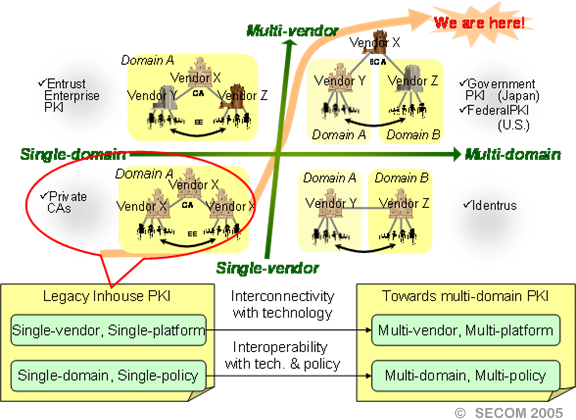
Figure2: What is a multi-domain PKI?
|
| Multi-domain PKI and interoperability |
|
To realize a multi-domain PKI environment, each PKI domain should specify their policy and the differences between their policy and other PKI domains. Thus the use-cases in establishing the trust model from inter operation are reflected in the Best Current Practice.Therefore we considered the following and submitted a proposal as a BCP to the IETF.
- Clarification of the trust relationship in PKI
- Definition of a PKI domain
- Model definition of a single-domain PKI
- Model definition of a multiple-domain PKI
A trust relationship in PKI can be classified into three models, an operation based trust list model, a certification based cross-certification model like the GPKI and a typical strict hierarchy model. The definition of a PKI domain is necessary to clarify the borders in a multi-domain PKI. Thus, to clarify the difference between PKI domains, we must define exactly what items must be clarified. Therefore, we modeled the typical cases in organizing a trust model for single-domain and multi-domain PKI and disseminated them as use-cases in establishing both single-domain and multi-domain PKI.
On top of this, interoperability for certification path validation is necessary to verify the evaluation of the difference of between policies in these trust models.
|
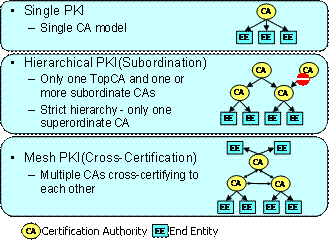
Figure3: Single-domain PKI model
|
|
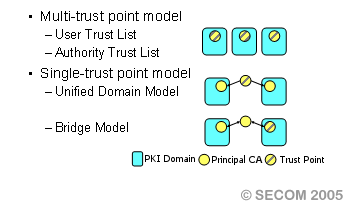
Figure4: Multi-domain PKI model
|
|
| Building the consensus for Best Current Practice |
|
In this way, there are still many unresolved issues in multi-domain PKI interoperability. To achieve interoperability easily for the various PKIs around the world, we should consider the issues from a worldwide viewpoint and document it as a Best Current Practice.
I am working to examine these issues and to build consensus worldwide. Secom, with experience in the Japanese government PKI (GPKI), and NIST, with experience in the US Federal Government PKI (Federal PKI) has shared our experiences and results for PKI interoperability and is submitting a proposal to the international standards body IETF for consideration as a international standard.
For the standardization activities, I am working with various educational campaigns both domestically and internationally to disseminate knowledge about PKI technology as a security baseline for the networking community. It is important to gather a consensus of not only Japan and the US but also from Europe, Asia and even domestic companies.

|

|
|
Presentation at the 57th IETF Meeting
(Mr.Stephen Kent (BBN, left), Mr.Tim Polk (NIST, center), author (right))
|
The luncheon meeting with Mr. Nelson Hasting at the 61st IETF Meeting
(From the left-hand side, author, Mr.Miyakawa(IPA Japan), Mr.Nelson Hastings(NIST)
|
|
| References |
- Shimaoka, M., NPO Japan Network Security Association, and ISEC, Information-Technology Promotion Agency, Japan, "Interoperability Issues for multi PKI domain", July 2002.
- NPO Japan Network Security Association and ISEC, Information-Technology Promotion Agency, Japan, "Implementation Problems on PKI", Feb 2003.
- Japan PKI Forum, Korea PKI Forum, PKI Forum Singapore, and Chinese Taipei PKI Forum, "Achieving PKI Interoperability 2003", July 2003.
- Japan PKI Forum, Korea PKI Forum, and PKI Forum Singapore, "Achieving PKI Interoperability", April 2002.
|
| Organizations |
- JNSA: NPO Japan Network Security Association Non-profit Organization working to raise awareness of the importance of network security.
JNSA works for various PKI interoperability such as PKI interoperability technology Working Group and "Challenge PKI" project.
- IPA: Information-Technology Promotion Agency Institutionalized in 2004 as Independent Administrative Organization.
Security engineering laboratory in IPA/ISEC(IT SEcurity Center) works for both solutions and promotions of various PKI technology commencing with establishment of operating policy of trust model in multi-domain PKI.
- IETF (Internet Engineering Task Force)
A large, open international community charged with developing and promoting Internet standards.
IETF standardizes PKI technology used in the Internet around PKIX(Public Key Infrastructure X.509) Working Group.
- NIST (National Institute of Standards and Technology)
A government agency of U.S. Department of Commerce.
NIST acts a primary role in U.S. Federal PKI and IETF/PKIX WG, and exercises the leadership for PKI worldwide.
|
| |
 |
|
|
|